Relying on a single line of defense to protect your network is a dangerous gamble. An attacker can circumvent any single defense measure. To most effectively protect your network and your valuable assets that within it, you need a defense in depth strategy.
Since your network isn't a fixed point, it's a territory, if an attacker invades a portion of your network you need the resources to detect and remove them. Combine multiple layers of defense measures to achieve the most robust network security.

“Network security combines physical security measures with software security measures to protect and maintain a network from unauthorized access and misuse. Network security preserves the usability and integrity of your network and data.”
Phishing is a malicious tactic used by hackers to trick their victims into handing over valuable information.
Hackers spend a lot of time crafting clever messages that appear so realistic that you wouldn’t think twice while looking at them.
Once the person who is being deceived has fallen for the attack, hackers can obtain what they were after; passwords, credit card information, direct access to your bank account, and even demands money.
Educate employees on the risks of opening suspicious emails and clicking on links within emails that may ask for information that is confidential or downloading unknown attachments.
Credential Theft is a rising epidemic that occurs when someone's proof of identity is stolen, be it physical or digital. When your credentials for one website are taken, it opens the door for your entire identity to be frauded.
Once an attacker has your usernames and passwords, they can sell them on the dark web or use them to compromise your organization's network.
Consider a dark web monitoring service to be alerted when your personal information is detected for sale in dark web market places. For stronger account security, implement multifactor authentication and make use of password managers. Authentication that relies on a username and password alone is too fragile.
Cryptojacking is an exploit in its infancy. It's a method used by hackers to mine cryptocurrency from their victim's computers. Cryptojacking code sits on infected websites and advertisements, auto-executing once the code loads in the affected victim's browser.
The code goes to work in the background of the victim's machine. The only indicator it presents to the end user is slower performance. This nasty infection was found on big websites including Showtime Networks and UFC Fight Pass.
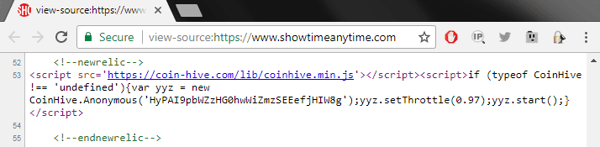
Cryptojacking malware was found on Showtime’s video streaming website. It was present for at least three days in 2017.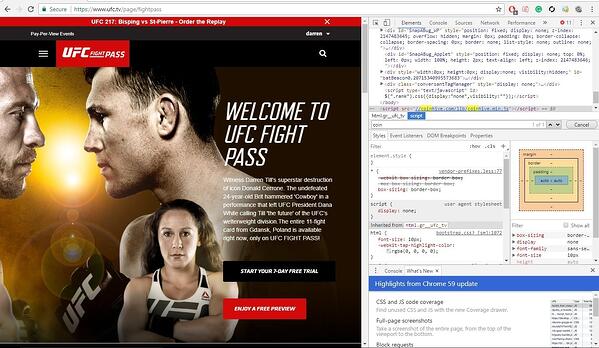
Subscribers to the UFC’s Fight Pass streaming service posted screenshots on social media of
Protect against single points of failure in your security stack by using overlapping defensive systems;
Unpatched software contains vulnerabilities that are exploited by hackers and is one of the most straightforward threats to manage. Commonly used programs like Adobe and O365 have vulnerabilities. When vulnerabilities are discovered patches are pushed out via software updates. The reluctance of end-users to update software and install patches can leave these vulnerabilities open for exploitation for far longer than they should be.
Update your software when prompted and install patches. Many MSSPs also offer complete patch management services to keep you up to date and protected.
Ransomware didn’t go away; it got more sophisticated and stealthier. Targeted ransomware can lock organizations out of essential systems and bring work to a halt. While these attacks are lucrative and sophisticated, the attackers aren’t looking for a challenge. Get the security basics right to stay off their hit list.
Give attackers a challenge. Lockdown RDP and assign user rights based on need. Implement overlapping layers of security on a well-segmented network
Breaches begin with human error. Network security at the
Having 100
Educate your employees, a little training goes a long way. Being proactive and empowering your employees with information is the best way to keep your security tight.
Not every user and device requires unrestricted access to your network. Using network access control is a quick way to mitigate your risks.
You can require devices to meet specific parameters, such as scanning clean or running a particular OS. You can allow or disallow network access based on these parameters.
Antivirus software is computer software that is used to prevent, detect, and remove malware. Initially developed to combat computer viruses, antivirus software has evolved to provide protection against various computer threats including trojan horses, ransomware, and keyloggers.
Email has made workplace communication efficient and convenient for everyone. While this has boosted the productivity of workers, it has also made hackers jobs easier.
Email security is the techniques and protocols that are in place to keep email communications secure against compromise, loss, or unauthorized access.
Firewalls have been the first line of defense in network security for nearly three decades. A firewall is a device that sits on a network to prevent traffic, people, and devices out on the internet from getting into your private network.
Firewalls are used to keep malicious activity and unwanted traffic off your network.
The landscape for mobile threats is rapidly expanding as an increasing number of workers connect some combination of a personal cellphone, laptop, and/or tablet to their corporate network.
Cybercriminals are aware of the increasing number of mobile devices connecting to enterprise networks, that's why nearly one-third of all fraud targets mobile devices.
You will need to configure their connections to keep network traffic private.
SIEM platforms give full insight into all systems within a particular environment. They have developed to address needs where security action is as necessary as security information.
SIEM takes all logging information from multiple systems and pulls them all together into a single place that can be monitored for best security practice.
A VPN keeps your network safe using end to end encryption. This encrypted tunnel ensures that your web browsing traffic, network transactions, and emails, remain confidential.
If you’re not using a VPN cyber voyeurs can intercept your data to use and abuse for their purposes.