
Managed IT Security
Cybersecurity and IT as a Service
Protect your network perimeter with layered threat defenses.
Managed IT Security & Strategy
Our Managed Security Solution is a user-based bundle of cybersecurity solutions and IT services that deliver layered protection and support for your organization. Gain the protection and guidance you deserve, from the industry's top talent.
PRODUCT FEATURE TWO
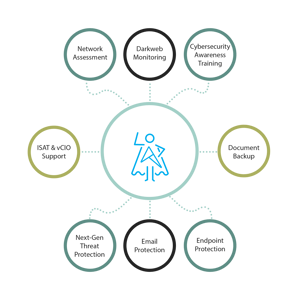
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. Lorem ipsum dolor sit amet.8 Layers of IT and Security

Our Model
The model was designed to deliver a predictable IT spend and help organizations focus on running their mission-critical business operations. Here's what we deliver:
Simple. Easy. Straightforward. Our user-based billing model eliminates cluttered, hard to read invoices. Each month you receive a clean and readable statement that ensures accuracy.
Our Everything-as-a-Service model (XaaS) significantly reduces costs and streamlines IT deployments. Your organization no longer needs to incur the expense of purchasing and maintaining expensive application servers and software. Less on-premise IT means less physical overhead.
The shortage of IT talent is one of the top emerging risks facing organizations. Hiring the right people internally to secure your business is a significant challenge. Augment and enhance your existing IT capabilities with our team's deep and diverse pool of knowledge.
The amount of software needed in business today expands across multiple functions, features, and vendors, making licenses one of the most challenging and expensive components of a cybersecurity plan. We handle all licensing issues by bundling our enterprise-security tools, taking the guesswork out of licenses at an economical price.
Security flaws at third-party vendors are one of your most significant security risks. Using a vendor that has weak security is like having a deadbolt on your door but leaving your window wide open. It's a natural entry point for bad actors. We vet every vendor to ensure tight security and compliance with an array of industry regulations.
Every organization needs a cybersecurity program. Establishing one on your own can be daunting. A dedicated vCIO will help you develop a strategic roadmap to keep your business and technology aligned. Our vetted processes and knowledge are tailored to your needs to achieve your desired business goals.